Eight critical use cases

As the retail industry continues recovering from the pandemic at a much more modest growth rate than in previous years, retail leaders are seeking new ways to prioritize customer experience. According to the National Retail Federation (NRF), 80% of shopping still happens in stores. But customers also demand omnichannel service and personalization to a degree not seen in previous generations. To meet these demands, retail leaders are turning to location-based marketing technology.
What is location-based marketing?
Location-based marketing (aka geospatial) technology is a set of tools for analyzing location data. Location-based technology leverages Global Positioning Systems (GPS), Geographic Information Systems (GIS), and Internet of Things (IoT) devices, such as cameras and sensors, to gain visibility into customer movements and behaviors.
Retail leadership and marketers can utilize location-based technology to:
- Better understand customer behavior.
- Analyze parking data.
- Identify market gaps and opportunities.
- Generate and test market predictions.
- Create targeted hyperlocal and personalized promotions.
This post will investigate eight use cases of location technology for retailers.
Also read: The future of retail: Securing app-driven stores
1. Location-based customer segmentation
Geographic segmentation divides customer bases by specific location demographics, i.e., country, state, county, city, or zip code. Regionally segmenting customers is helpful. However, it can overlook cultural nuances, especially in a population-dense area.
Geofencing and geotargeting take this concept down to a hyperlocal scale, zooming into a city, neighborhood, storefront, or area surrounding a storefront.
- Geofencing creates a virtual boundary around a specific area. Once inside the area, a customer may receive targeted promotions. For example, a customer who enters a geofence around a grocery store may receive a text message coupon or an in-app promotion.
- Geotargeting often incorporates geofencing but relies on additional customer data, such as behavior and interests, to further refine who receives promotions and messaging. Say a regional restaurant chain is launching a new vegetarian menu. Marketers could target customers with a city geofence and then further home in on vegetarians and healthy eaters. In other words, vegetarians within Cleveland would receive a series of promotions once they entered the city or geofenced region.
2. Foot traffic analysis and heat mapping
IoT sensors and cameras are revolutionary in generating real-time data that retailers can utilize to dive into the customer’s mindset. Additionally, retailers can draw on Wi-Fi and GPS beacon data to create heat maps (graphic representations of the most-visited versus the least-visited areas).
Retailers utilize heat maps and foot traffic analysis to:
- Plan store locations: Measuring visits to a property, determining the trade area, or analyzing the audience’s demographics are some of the common uses of data to gain insights into a location’s visitors (more on this in section 3).
- Understand store traffic: Utilize geospatial data to analyze foot traffic patterns, peak visiting hours, and popular areas within stores.
- Visualize data: Identify hotspots and optimize store layouts, product placements, and promotional displays for better engagement.
- Experiment with product staging: Heat maps can help identify zones of interest and help you optimize planograms and displays to generate interest and sales.
3. Market analysis and site selection
Geospatial data provides valuable insights for businesses looking to assess market potential, understand consumer demographics, and optimize store site selection. Spatial analysis combines geographic and descriptive data from various sources and uses geographic models and visualizations to provide insights beyond traditional GIS frameworks. Companies can gain BI-based insights on individual stores, departments, and product categories by leveraging cloud computing, geospatial data, on-demand analytics, and rich reporting.
This strategy enables property managers to incorporate point-of-sale data into their selection and forecasting models and includes previously impractical data on urban storefronts, shopping centers, end caps or pads, parking, view corridors, and zoning.
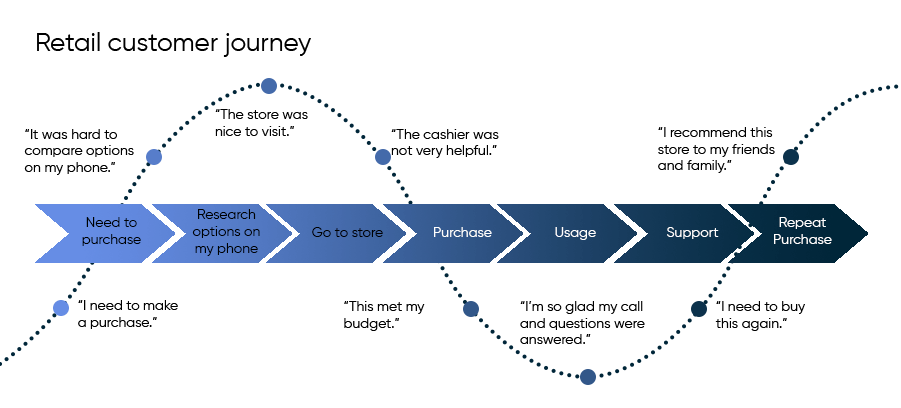
4. Customer journey mapping
Mapping the customer journey from home to store or within a shopping center can help refine marketing strategies. Creating a visual representation of every customer engagement with a brand can help avoid potential issues, increase customer retention, and make informed decisions. The map can be used to train team members, present visual diagrams in company-wide meetings, include the sales team in the map assessment and review the map with the customer service team to reduce obstacles throughout the customer lifecycle.
Based on the insights from a detailed journey map, businesses can combine online and offline marketing efforts to drive foot traffic to retail stores, utilizing digital channels like social media ads, email campaigns, and local SEO to reach a wider audience. Meanwhile, traditional tactics like direct mail, print ads, and community partnerships can increase brand awareness and attract local customers. This creates a comprehensive marketing mix that maximizes reach and drives sales.
5. Proximity marketing and hyper-personalization
Utilizing geofencing and geotargeting allows retailers to trigger real-time personalized offers or notifications to customers’ mobile devices when they are in proximity to a store or specific location. Marketers combine location-based data with customer preferences to deliver highly targeted and relevant marketing messages, enhancing engagement and conversion rates.
Proximity marketing technologies include:
- Wi-Fi to collect data.
- GPS for geofencing.
- NFC for contactless communication.
- Bluetooth beacons to detect nearby devices and send location-based messages.
Proximity marketing offers tailored advertising, personalization, data collection, and app engagement. Real-time targeting delivers personalized advertising messages to the right audience at the right time based on data.
Personalization can increase revenue and conversions, improve customer lifetime value, reduce churn, and increase revenue. According to Boston Consulting Group, retailers with advanced personalization capabilities saw a consistent 25% increase in revenue, and a stunning 110% of customers are more likely to add more items to their basket if the experience is personalized.
6. Competitive analysis and benchmarking
Retailers utilize location-based marketing technology to analyze competitors’ locations and foot traffic patterns to gain insights into consumer behavior, helping refine strategies and stay competitive. They can also create performance benchmarks that compare store performance and consumer engagement metrics against competitors in specific geographic areas to identify areas for improvement.
When conducting competitive benchmarking, businesses typically consider the following metrics:
- Customer engagement on social channels.
- Brand awareness.
- Customer experience ratings, such as satisfaction, ease of use, etc.
- Search engine results.
- Reviews.
- Revenue.
7. Predictive analytics and forecasting
Retail predictive analytics is the practice of using historical data to anticipate customer behavior and make informed decisions. Use geospatial data in predictive analytics models to forecast future consumer behavior, enabling proactive decision-making and resource allocation. Demand Forecasting predicts demand patterns based on geographic trends and consumer behavior to optimize inventory and supply chain management.
It’s essential to remember that the accuracy of retail analytics output directly depends on the quality of data used to generate it. Hence, it’s crucial to carefully evaluate the data sources before utilizing them for analysis.
8. Compliance and ethical data use
A majority of states in the U.S. have some data privacy laws in place with approximately a dozen states with comprehensive compliance regulations in place. Privacy regulations apply to all retailers, and strategies aim to protect customer data integrity, physical privacy of payment cards, deletion rights, unauthorized access, and customer information sharing. Policymakers must adjust their approach according to their business model and vulnerabilities.
Working with the right technology partner can ensure compliance with data privacy regulations when collecting and utilizing geospatial data, prioritizing customer privacy and consent in location-based analytics.
Additionally, retailers must maintain transparency with customers about data collection practices, ensuring they understand the value proposition and benefits of sharing location information. Implementing modern physical and digital security measures can improve customer trust and loyalty. A secure database is vital for retailers to maximize customer relationship management and identify business development opportunities.
Watch: Tech Talk: Building the “storefront of the future”
Putting it all together
In today’s retail industry, keeping up with the latest technology trends is crucial to stay competitive. However, for those not directly involved in the IT side, such updates can be disruptive to the day-to-day functioning of the store. Therefore, you must partner with an experienced technology provider who can help your team plan and implement location-based marketing tools and then seamlessly transition into a support or managed services role. By implementing cutting-edge technology, retailers can stay up and running smoothly, generating new avenues of revenue for the business.
At CBTS, we have years of experience working with all types of retail establishments. Contact us today to learn how we can help you improve your customer experiences and boost revenue with location-based technology solutions.






