
What is cloud security?
A recent study found that the global cloud services market is valued at $454 billion and is expected to surpass $2 trillion by 2032. As businesses continue to shift toward cloud integration, security becomes more and more urgent. Even though the Cloud is much more secure than traditional on-premises data centers, vulnerabilities still exist. These vulnerabilities make investing in cloud security services vital.
What exactly is cloud security? Cloud security is a set of tools, frameworks, and protocols to protect data (in motion and at rest) from unauthorized access, theft, or malware threats. Cloud security spans assorted technologies to defend public, private, and multi-cloud environments, whether Infrastructure as a Service (IaaS), Software as a Service (SaaS), or Platform as a Service (PaaS).
When configured correctly, cloud-integrated security keeps organizations profitable by defending against the negative ramifications of a data breach, such as losses in paid ransom, reputational damage, regulatory action such as fines or license suspension, as well as guarding end-user data. Like other elements of cloud computing, your security team becomes cost-efficient by switching from the capital expense model to operating expenses. Bills come from small, monthly subscriptions and service fees instead of costly, upfront investments.
Why integrated cloud security is vital
If cloud computing is more secure than on-prem, why worry about it? Gartner calculated that organizations lose an average of $5,600 per minute of downtime experienced from a malware attack. Besides shrinking your attack surface and lowering the likelihood of a breach, cloud security can help maintain business continuity in the event of a successful breach or natural disaster. Data protection services such as managed backup and Disaster Recovery as a Service (DRaaS) ensure minimal downtime and maintain data compliance.
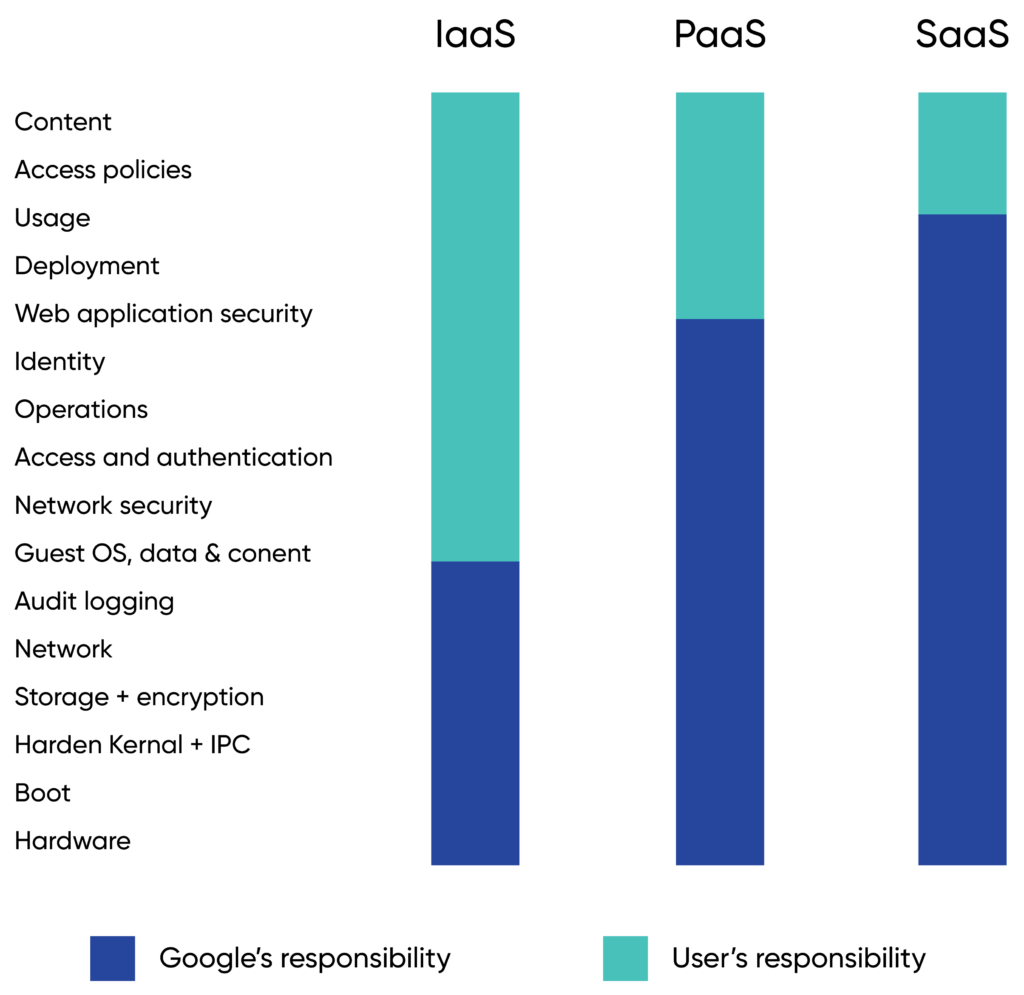
The shared responsibility model
Cloud security utilizes the shared responsibility model, in which a cloud service provider (CSP) and the customer share the burden of defending cloud systems. Confusion sometimes arises about who exactly is responsible for what.
There are minor differences between each CSP and which model of cloud you choose: IaaS, PaaS, SaaS, or some combination of all three.
Generally, the cloud service provider is responsible for the security of:
- Data.
- User identities.
- Identity.
- Physical networks.
- Servers and storage.
- Hypervisors.
The customer is responsible for securing the following:
- Operating systems.
- Virtual networks.
- Applications.
- User data.
- Operations.
- People and employees.
Note that network security is the customer’s responsibility in IaaS.
Benefits of cloud security
- Lower costs – Cloud data security can lower costs and reduce administrative burden.
- Cost-efficiency – Cloud-integrated security helps to shift spending models from CapEx to OpEx, resulting in cost savings.
- Greater visibility – Robust security measures for cloud data offer insights into the internal operations of your cloud environment, such as identifying data assets and their location, monitoring user activity, and tracking the type of data being accessed.
- Backups and recovery – Cloud data security offers automated and standardized backup solutions, freeing your teams from monitoring manual backups and troubleshooting problems.
- Cloud data compliance – Effective cloud data security programs ensure conformity with data compliance laws and regulations by monitoring data storage, access, processing, and protection.
- Data encryption – Cloud service providers implement advanced encryption for securing sensitive data in transit and at rest.
- Advanced incident detection and response – Cloud providers invest in cutting-edge AI technologies and security analytics to quickly identify and respond to security incidents.
Challenges of implementing cloud security
Unlike the digital security models of the past, the Cloud does not have a defined perimeter. The castle-and-moat model, in which a firewall is established around a data center, is ineffective for the Cloud because each point of presence (PoP), application, and network represents potential weak points.
Other challenges to cloud security include:
- Lack of visibility – Without proper implementation, some companies struggle to locate all their data and applications and identify their assets.
- Less control – As data and applications are hosted on third-party infrastructure, companies have less control over how data is accessed and shared.
- Confusion over shared responsibility – Organizations and CSPs share security responsibilities, which can lead to vulnerabilities if the roles are unclear.
- Malware and ransomware – Sensitive data stored in the Cloud is a tempting target for cybercriminals, especially companies with extended supply chain connections.
- Compliance regulations – Increasingly, regulators like HIPAA, the FTC, and the SEC are cracking down on data compliance rules, including how soon an organization must report a data breach.
- Misconfigurations – Misconfigurations and human error continue to be a leading cause of catastrophic data breaches.
Guiding frameworks and pillars of cloud security
Known as the CIA triad, cloud data security follows the same guidelines as information security:
- Data confidentiality – Sensitive data should only be accessed by authorized users.
- Data integrity – Data is accurate and free from tampering or sabotage.
- Data availability – Data is continuously available to verified users.
A data breach violates one or more of these tenets. The CIA triad is a valuable tool security professionals utilize in organizational risk assessment. Additionally, the NIST has created another assessment tool, the Five Pillars of Cybersecurity. They include:
- Identify.
- Protect.
- Detect.
- Respond.
- Recover.
At CBTS, we build on this assessment tool and define our own six pillars of cloud security:
- Security assessments.
- Cloud monitoring and management.
- Managed backup.
- Disaster recovery.
- Patch management.
- Cloud security posture management.
Learn more: The six pillars of cloud security
Yet another framework that guides cloud security is zero trust. The concept of zero trust in cloud security was introduced in 2010 by Forrester. It emphasizes not trusting anyone or anything within or outside the network. Instead, everything needs to be authorized, inspected, and secured. Zero trust promotes a least privileged governance strategy and requires developers to fortify web-facing applications properly. Micro-segmentation is also used to create secure zones and traffic between them.
Key cloud-integrated security technologies
- Disaster recovery and backup – Properly configured and tested disaster recovery minimizes downtime in case of a breach or disruption from a natural disaster or other causes.
- Threat detection – AI-powered XDR and SIEM seek out and destroy threats before they have a chance to create a breach.
- Data loss prevention (DLP) – DLP solutions help organizations classify and protect sensitive data by identifying policy violations and enforcing remediation through alerts, encryption, and other protective actions.
- Cloud security posture management (CSPM) – Addresses misconfigurations and limited visibility by deploying automation for continuous monitoring and increased visibility.
- Cloud access security broker (CASB) – A tool that bridges the gap between cloud service consumers and providers. It extends security controls from on-premises infrastructure to the Cloud, enforcing security, compliance, and governance policies for cloud applications. CASB can be hosted either on-prem or in the Cloud.
- Identity and access management (IAM) – This feature merges multi-factor authentication (MFA) and user access policies, restricting data access to verified users.
- Vulnerability and penetration testing – Identifies potential weaknesses or exploits to improve security postures.
- Micro-segmentation – This feature divides cloud deployments into distinct security segments—from the network level down to the individual workload level—mitigating damage in the event of a successful attack.
- Next-generation firewalls – Secure workloads by deploying advanced firewall capabilities at the network edge, such as intrusion prevention, deep packet inspection, application control, and encrypted traffic analysis, for comprehensive threat detection and prevention.
Seeking out a security partner
No single technology or solution fully encompasses integrated cloud security. The key is appropriately implementing and integrating cloud security tools and creating greater efficiencies between them for the most robust security posture possible. Even with the enhanced security offered by CSPs, your organization needs to fully understand where it’s protected in service-level agreements (SLAs) and where potential vulnerabilities lie. The best way to do so is to partner with an experienced cloud security vendor.
With years of experience managing enterprise data centers on-prem and in the Cloud, CBTS delivers the latest technologies in managed cloud security services and backup solutions. Our team maintains relationships with top CSPs and security providers to offer comprehensive protection against cyberattacks and downtime. At CBTS, we strive to understand your unique business challenges and provide the necessary expertise, training, and certifications to protect your business from data breaches, theft, and other common causes of system outages.




















