
I sat down with two experts from Check Point Harmony, Chris Bernard, MSSP Sales Manager Email Security, and Paul Welford, MSSP Lead Solutions Architect, to explore methods of fighting phishing attempts and securing your e-mail setup. Discover cutting-edge strategies and how Check Point’s Harmony Email & Collaboration (HEC) assists in keeping you ahead of emerging email threats.
Despite the rise of file sharing, storage, and messaging apps, e-mail remains the dominant form of digital communication in business. Given the number of cyber threats explicitly targeting e-mail accounts, the issue of e-mail security is more pressing than ever. Cloud-based e-mail providers have some security baked in, but ultimately, each company is responsible for implementing strong security measures to protect sensitive information shared through email and account permissions.
Avanan, now a part of Check Point Harmony Email & Collaboration (HEC), pioneered API-based e-mail security and holds a patent for its unique inline deployment method via API. It has continued to lead the industry by offering unparalleled capabilities and performance among other API-based e-mail security solutions.
This discussion aims to illuminate the concept of API e-mail security, its significance, and how it enables organizations to secure e-mail communications effectively.
A quick history of e-mail security solutions
In the early 2000s, Secure e-mail gateways (SEGs) emerged to secure enterprise e-mail communications. SEGs relied on MX records, which Paul urged us to consider as a mailbox in front of the house. “The mailman doesn’t deliver the information directly to your door anymore,” Paul said. “He drops it off at the mailbox in the yard, and then you go up there, and you pick it up. Imagine that mailbox having a giant security system. You have to route your traffic to that. So technically you have to take down mail traffic to route it to that point before it gets to your house. There’s potential for some issues there.”
In other words, SEGs reroute e-mail traffic through a gateway before the e-mail is delivered to an inbox, in the same way, a mail carrier would travel through a metal detector before delivering mail to a government office. When enterprise e-mail servers were primarily based on-premises, this was a fine system, but once everything began migrating to the Cloud, attack vectors emerged that SEGs could not protect against.
API-based e-mail protection emerged as an alternative. API-based e-mail integrates into the e-mail program rather than rerouting traffic. Additionally, inline e-mail security evolved as the next step from e-mail gateways. Inline security lies “along” the e-mail path and scans the message before delivery.
SEG vs. Inline API vs. post delivery API-based e-mail security solutions
- Secure e-mail gateways – The legacy approach to e-mail security that sends mail traffic through a virtual gate to scan for malware before delivering messages into the inbox. This approach has latency issues and is inadequate to defend against modern threats.
- Inline API – An updated version of SEGs, inline security also scans e-mails before inbox delivery.
- API-based – This type of security utilizes the API of email programs to defend against various threats. Rather than implementing e-mail security systems inline with the corporate e-mail server, API-based e-mail security integrates directly with the e-mail program to provide protection against or warn about possible dangers. API-based security scans messages after delivery.
HEC combines API-based and inline approaches for maximum security and advanced AI engine protection.
Learn more: Why use Harmony Email & Collaboration
The challenges facing e-mail customers today
Many organizations are saddled with outdated e-mail security solutions that must be updated for the current threat landscape. Chris said, “It all goes back to visibility. Those secure e-mail gateways and legacy approaches aren’t cloud native. Being native to the Cloud gives us complete visibility into the environment.”
That visibility is more critical than ever with emerging threats, including:
- Malicious URLs and QR codes.
- Phishing attempts and advanced social engineering schemes powered by generative AI.
- Account takeovers and insider threats.
- Advanced impersonation attacks enabled with deep fake technology.
- Message-based malware in which no file or URL needs to be clicked or downloaded.
- Post-arming delivery tactics that bypass inline and SEG defenses.
Additionally, organizations must manage compliance concerns and ever-growing regulatory scrutiny.
The Check Point Harmony Email & Collaboration (HEC) solution
Check Point Harmony Email & Collaboration is a patented and novel approach to email security that merges API-based with inline security methods to provide the benefits of both. HEC deploys artificial intelligence (AI), machine learning (ML), and human security oversight to catch the threats that slip through legacy systems.
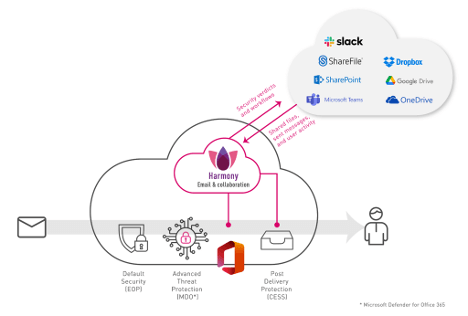
Download our info sheet to learn more about how Harmony Email & Collaboration works.
How HEC stands out
- Check Point has adopted the philosophy of “Prevention First,” which aims to keep threats out of your inbox, with added safeguards for automatic post-delivery forensics and protection.
- Swift implementation. Our guest experts said, “Just seven clicks and 30 seconds, you’re up and running.”
- Cloud-native security means up-to-the-minute updates that keep your inbox current with evolving threats and prevent zero-day attacks.
- Integrates with Google Workspace and Microsoft 365.
- Secures leading messenger collaboration tools like Slack and Microsoft Teams.
- 99.8% efficacy rate.
- Cutting-edge AI and ML power by Check Point’s Thread Cloud AI, supervised by e-mail security experts.
- HEC can rewrite and disable malicious URLs and QR codes before reaching the end users inbox.
Check Point Threat Cloud AI issues six billion daily verdicts for previously unknown malware.
How HEC uses AI
HEC utilizes dozens of AI and ML tools to automatically detect and quarantine phishing and other malicious content without requiring user or security analyst intervention. As Paul mentioned, the “brains” behind the HEC solution is the Infinity ThreatCloud AI from Check Point.
Paul elaborated, “Essentially the way ThreatCloud functions is it takes the technology or the signatures or the scans or all of these attacks that they see from other platforms, like their firewall, cloud guard, their endpoint management solutions, mobile device management solutions, any attacks it sees there, they dump into ThreatCloud… A malware message comes in, we go through a signature-based scan—but then it also hits our sandbox, goes through a zero-day scanning process, and that zero-day scanning process also takes the intelligence from ThreatCloud.”
The CBTS and Check Point partnership
One thing I have recognized in working with Check Point over the last few years is that their innovation cycle is fast. Security evolves faster than other industries, and Check Point’s speed allows it to stay right on top of the latest technology and to effectively counter emerging threats. Check Point has been a very valuable partner for CBTS, and we are excited to continue working with them to stop malware threats to your inbox with a near 100% success rate.
Interested in a live demo of the Check Point Harmony Email & Collaboration security solution? Contact us to schedule one.





















