
In my previous blog post I talked about the MITRE ATT&CK framework and how it helps you determine possible threats and threat actors’ techniques so that you can better focus your limited resources on the more likely threats.
The next question you might have is, “Am I being attacked?” and “Are my defenses working?” To answer that question you need to know what is happening on your network. To know what is happening you need to log activity on your network from a few sources.
Take your typical network that consists of a wired network (the PC connected to the switch) and some wireless laptops (connected to the wireless access point). The switch and the access point connect to a router and then to the firewall.
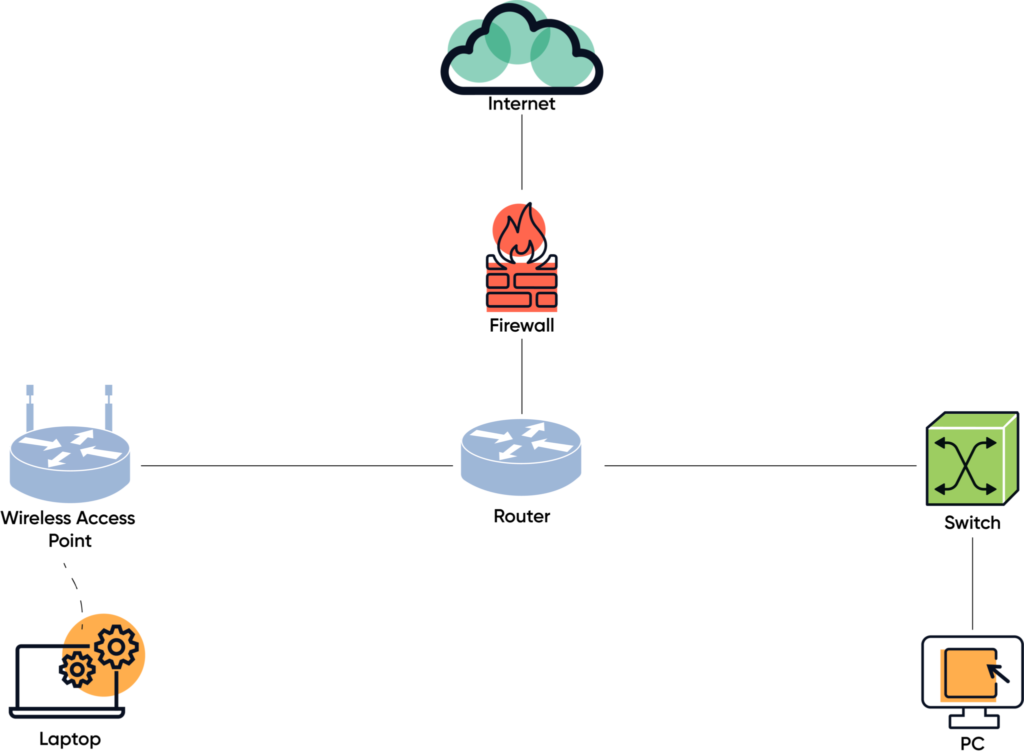
If you want to know what is going on your network, you want to see the network activity (traffic) that is flowing on the wireless access point, the switch, the router, and the firewall. To do that you have to log what devices and traffic are on your wireless network and wired network, as well the flow of traffic between the wired and wireless network, and the flow of traffic between the router and the firewall.
Typically you would have the access logs or system logs from each of these devices sent to a central collector, called (surprise!) the system log server, or syslog server. Your network would now look something like this:
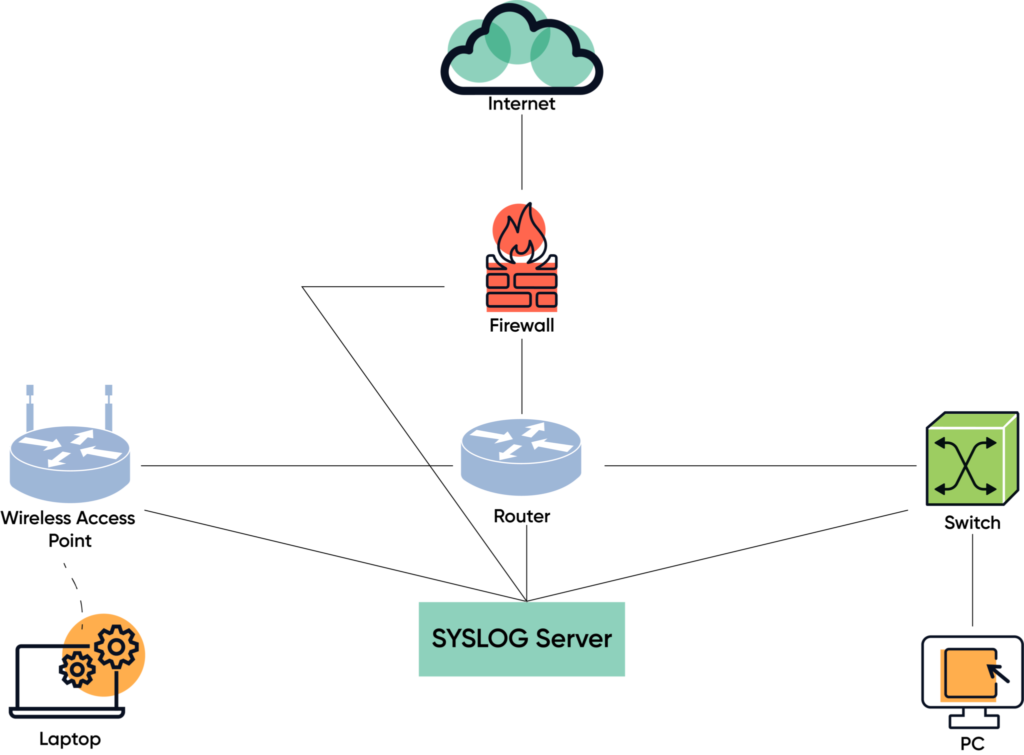
Now that you are collecting this traffic information on a daily basis, you can then run searches (usually automated) that look at the log data and tell you if some odd or suspicious traffic is on your network.
You can search the syslog server for bad traffic coming from the internet to your firewall and confirm that the firewall is blocking the traffic. Or, you can confirm that you only allow certain kind of network traffic to leave your network to prevent private or sensitive data from leaving your network (think PII, HIPAA, intellectual property, CUI, etc.) via DropBox or Google Drive or Box. By checking the firewall logs you can tell that your data is not leaving your network through the firewall.
You can search the syslog server for unknown devices on the wireless or wired network. You would know which devices should be on the network, because you know what devices you own or have provisioned for your users to use. If a device shows up in the wireless log or the wired (switch) log you then know that you have to find out what that device is. How did it get there? Did someone bring in their own wireless access device so they can get a better signal in their office? Did they bring in a wireless printer so they can print in their office? By looking at the logs for those two networks you can determine that.
Your network team knows if traffic from the wired network should be allowed to flow to the wireless network, or flow the other way around. Maybe you allow that kind of traffic flow, maybe you don’t. Either way with a syslog server you can confirm that only allowed traffic is flowing on the wireless or wired networks by looking at the traffic logs from the router.
This is a simple example to help you visualize how collecting this network traffic allows you to see if the controls (access control lists [ACLs], firewall rules, network access control [NAC] rules, etc.) are working as you expect.
In my next blog post I’ll add in other data points (anti-virus software, Windows event logs, web server logs, etc.) to the syslog server to give you an even better picture of what is happening on your network.
Need help with your cyber defense? Contact the CBTS cybersecurity team today.
More from CBTS Consulting CISO John Bruggeman’s blogs:
What do new TSA requirements mean for the security of your critical infrastructure?
How do you ensure the security of your supply chain?
Can you be ransomware-proof? Is that even possible?
Getting ransomware-proof, continued: CIS controls for medium-size organizations




















